Tech Tip Tuesday: Wipe Before You Recycle
Tech Tip Tuesday: Wipe Before You Recycle Old laptops, smartphones, and hard drives hold more than outdated files. They often store sensitive business data, logins,
Stay ahead of cyber risks with expert insights, weekly threat analysis, and practical security guidance. Our blog delivers actionable intelligence for SMBs, CISOs, and IT leaders looking to strengthen their defenses.

Tech Tip Tuesday: Wipe Before You Recycle Old laptops, smartphones, and hard drives hold more than outdated files. They often store sensitive business data, logins,
Cyber Threat Intel – Monday Briefing Your weekly intelligence update on top threats, vulnerabilities, and emerging actors. August 18, 2025 Read the Full Report Executive

Stop Phishing Emails Before They Hit Your Inbox Cybercriminals still rely on phishing more than any other tactic to trick employees and gain access to

Overview Over the past few weeks, our Incident Response and SOC teams have detected a widespread phishing campaign targeting primarily U.S.-based organizations, including those in

When a user reaches out for a password reset or account assistance, your support team becomes the gatekeeper – balancing usability with the critical responsibility

“Global Threats, Local Impact: This Week’s Cyber Risk Update” This past week has been a loud reminder that cyber threats are growing in speed, scale,

CVE-2025-53770: “ToolShell” RCE Hits On-Prem SharePoint Servers Summary A critical remote code execution vulnerability—CVE‑2025‑53770—has emerged, targeting on-premises Microsoft SharePoint. Discovered as part of an attack
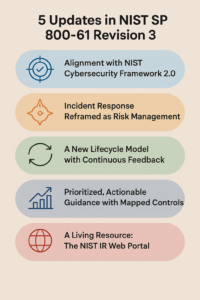
NIST has released SP 800-61 Revision 3, redefining incident response for today’s threat landscape. Learn the 5 biggest changes, why they matter, and how SOClogix can help you align your IR plan with the new NIST Cybersecurity Framework 2.0.

Every year, the Verizon Data Breach Investigations Report (DBIR) serves as a pulse check on the state of cybersecurity, and the 2025 edition pulls no

Your Organization Needs a Hybrid Approach to Penetration Testing Your organization is constantly up against new and evolving threats. Daily threat actors adapt their tactics,